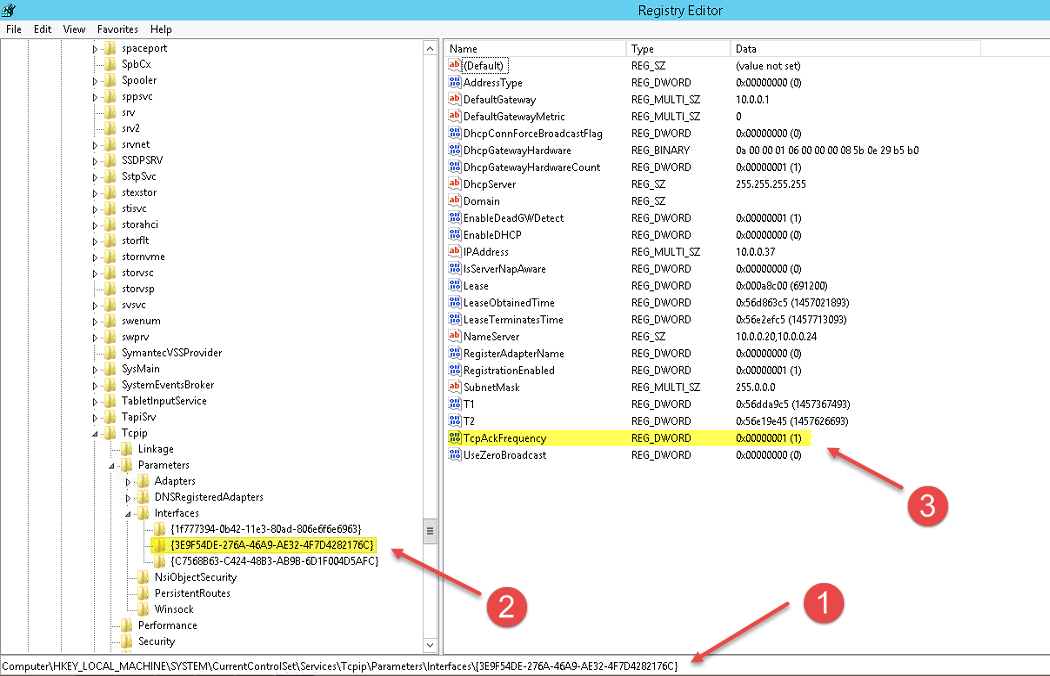
Edit Local Group Policy With Power Shell Array
IDM Power Tips. Often users have requested more in-depth information regarding specific features supported in our applications, and we now maintain an archive of.
Search the audit log in the Office 3. Security & Compliance Center - Be sure to read the following items before you start searching the Office 3. You (or another admin) must first turn on audit logging before you can start searching the Office 3. To turn it on, just click Start recording user and admin activity on the Audit log search page in the Security & Compliance Center. You only have to do this once. Note: We’re in the process of turning on auditing by default.
Until then, you can turn it on as previously described. You have to be assigned the View- Only Audit Logs or Audit Logs role in Exchange Online to search the Office 3.
By default, these roles are assigned to the Compliance Management and Organization Management role groups on the Permissions page in the Exchange admin center. To give a user the ability to search the Office 3. Exchange Online, add the View- Only Audit Logs or Audit Logs role, and then add the user as a member of the new role group. For more information, see Manage role groups in Exchange Online.
Edit Local Group Policy With Power Shell Array Functions
Edit Local Group Policy With Power Shell Array Methods
- Greenpeace will never stop fighting for a greener, healthier world for our oceans, forests, food, climate, and democracy—no matter what forces stand in our way.
- 6 Command Line Options. WeiDU is a command-line utility. GUIs are available, but this document only describes command-line invocation. Use the DOS Shell ("command" or.
Important: If you assign a user the View- Only Audit Logs or Audit Logs role on the Permissions page in the Security & Compliance Center, they won't be able to search the Office 3. You have to assign the permissions in Exchange Online. This is because the underlying cmdlet used to search the audit log is an Exchange Online cmdlet. If you want to turn off audit log search in Office 3. Power. Shell connected to your Exchange Online organization. Set- Admin. Audit. Log. Config - Unified.
Audit. Log. Ingestion. Enabled $false. To turn on audit search again, you can run the following command in Exchange Online Power. Shell. Set- Admin.
Audit. Log. Config - Unified. Audit. Log. Ingestion. Enabled $true. For more information, see Turn off audit log search in Office 3. As previously stated, the underlying cmdlet used to search the audit log is an Exchange Online cmdlet, which is Search- Unified.
Audit. Log. That means you can use this cmdlet to search the Office 3. Free Movie Download App For Mac on this page. Audit log search page in the Security & Compliance Center. You have to run this cmdlet in remote Power. Shell connected to your Exchange Online organization. For more information, see Search- Unified.
Audit. Log. If you want to programmatically download data from the Office 3. Office 3. 65 Management Activity API instead of using a Power. Shell script. For more information, see Office 3.
Management Activity API reference. You can search the Office 3. It can take up to 3. The following table shows the time it takes for the different services in Office 3. Office 3. 65 service.
Share. Point Online and One. Drive for Business.
Exchange Online. Azure Active Directory (user login events)Azure Active Directory (admin events)Sway. Power BIYammer. Security & Compliance Center. Microsoft Teams. As previously stated, Azure Active Directory (Azure AD) is the directory service for Office 3.
The unified audit log contains user, group, application, domain, and directory activities performed in the Office 3. Azure management portal. For a complete list of Azure AD events, see Azure Active Directory Audit Report Events. Return to top. Here's the process for searching the audit log in Office 3. Step 1: Run an audit log search. Step 2: View the search results.
Step 3: Filter the search results. Step 4: Export the search results to a file. Step 1: Run an audit log search. Go to https: //protection. Sign in to Office 3. In the left pane, click Search & investigation, and then click Audit log search.
The Audit log search page is displayed. Note: As previously explained, you have to first turn on audit logging before you can run an audit log search. If the Start recording user and admin activity link is displayed, click it to turn on auditing. If you don't see this link, auditing has already been turned on for your organization. Configure the following search criteria: Activities Click the drop- down list to display the activities that you can search for.
User and admin activities are organized in to groups of related activities. You can select specific activities or you can click the activity group name to select all activities in the group. You can also click a selected activity to clear the selection. After you run the search, only the audit log entries for the selected activities are displayed.
Selecting Show results for all activities will display results for all activities performed by the selected user or group of users. Cara Download Video Youtube Mpeg Dash. Over 1. 00 user and admin activities are logged in the Office 3. Click the Audited activities tab in this topic to see a list of descriptions of each activity for the different Office 3. Start date and End date The last seven days are selected by default. Select a date and time range to display the events that occurred within that period. The date and time are presented in Coordinated Universal Time (UTC) format.
The maximum date range that you can specify is 9. An error is displayed if the selected date range is greater than 9.
Tip: If you're using the maximum date range of 9. Start date. Otherwise, you'll receive an error saying that the start date is earlier than the end date. If you've turned on auditing within the last 9. Users Click in this box and then select one or more users to display search results for. The audit log entries for the selected activity performed by the users you select in this box are displayed in the list of results.
Leave this box blank to return entries for all users (and service accounts) in your organization. File, folder, or site Type some or all of a file or folder name to search for activity related to the file of folder that contains the specified keyword. You can also specify a URL or part of a URL to display entries for activity on any object in the specified URL path. Note that special characters, such as forward slashes (/), back slashes (\), dashes (- ), and underscores (. Be sure to replace special characters with a space. For example, to search for activity in a One. Drive for Business site, such as https: //contoso- mysharepoint.
When the search is finished, the number of results found is displayed. Note that a maximum of 1. Return to top. Tips for searching the audit log. You can select specific activities to search for by clicking on the activity name. Or you can search for all activities in a group (such as File and folder activities) by clicking on the group name. If an activity is selected, you can click it to cancel the selection.
You can also use the search box to display the activities that contain the keyword that you type. You have to select Show results for all activities in the Activities list to display entries from the Exchange admin audit log. Events from this audit log display a cmdlet name (for example, Set- Mailbox) in the Activity column in the results. For more information, click the Audited activities tab in this topic and then click Exchange admin activities. Click Clear to clear the current search criteria. The date range returns to the default of the last seven days.
You can also click Clear all to show results for all activities to cancel all selected activities. If 1. 00. 0 results are found, you can probably assume there are more than 1. You can either refine the search criteria and rerun the search to return fewer results, or you can export all of the search results by selecting Export results > Download all results. Return to top. Step 2: View the search results. The results of an audit log search are displayed under Results on the Audit log search page. A maximum of 1. 00. The results contain the following information about each event returned by the search.
Date The date and time (in UTC format) when the event occurred. IP address The IP address of the device that was used when the activity was logged.
The IP address is displayed in either an IPv. IPv. 6 address format. User The user (or service account) who performed the action that triggered the event.
Activity The activity performed by the user.